When the
- If none of the rules are true, it will perform the default action for the route, typically allow the traffic.
- If one of the rules is true, it will perform the actions and stop applying further rules.
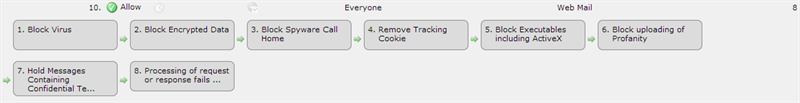
Consider the following content rules as they are applied to the Everyone to Web Mail route:
- Any traffic passing through this route that does not match another route will be allowed unless one of the rules is true
- Any traffic passing through this route that contains a virus will cause content rule 1, Block Virus, to be triggered. The traffic will be blocked.
- Any traffic passing through this route that contains encrypted files will cause content rule 2, Block Encrypted Data, to be triggered. The traffic will be blocked.
- And so on until the end of the rules.
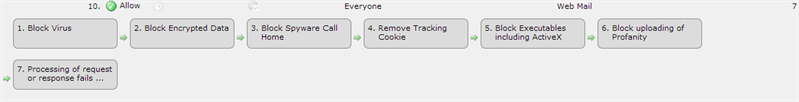
It is important that rules for a given route are configured in the right order. This is important when considering the level of threat and machine processing time and resources. The greater the threat, the higher the rule should be on the rules table.
Consider the following content rules as they are applied to the Everyone to Web Mail route:
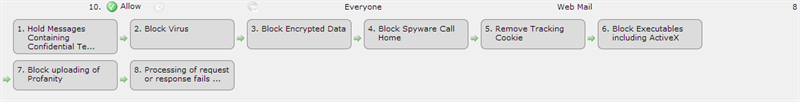
The first rule will scan the traffic looking for keywords as configured in the rule. However, there is little point in doing this because the second rule will block the traffic if a virus is detected.
A more efficient and safer order for this set of rules would be to place this rule after rules that deal with specific threats: